All of a sudden, nothing works anymore! A cyberattack has paralyzed your company’s systems. And it doesn’t matter whether the data has been encrypted, exfiltrated or backup copies have been made useless: the damage is severe, and the collateral damage can continue for a long time. Sometimes, an attack may have been prepared, unnoticed over several months, before it actually starts. This means that the cyber criminals were hiding in your system for a long time and know about and control many of your tools, apps, and accounts. Now it’s important to act rapidly and strategically to prevent the loss of your entire infrastructure. Compromise recovery is the way to go:
Regain control – and keep it in the long term!
Compromise recovery means returning control over its systems to an organization after an infiltration in such a way that control can be permanently maintained. This is usually achieved by changing a number of security settings, workflows, and use habits. Within an extremely short period of time, the company often has to make up for what it neglected for a long time. A challenge – even for the administrators of the relevant organization. They usually have to change their way of working and better understand where the especially dangerous vulnerabilities in the system are.
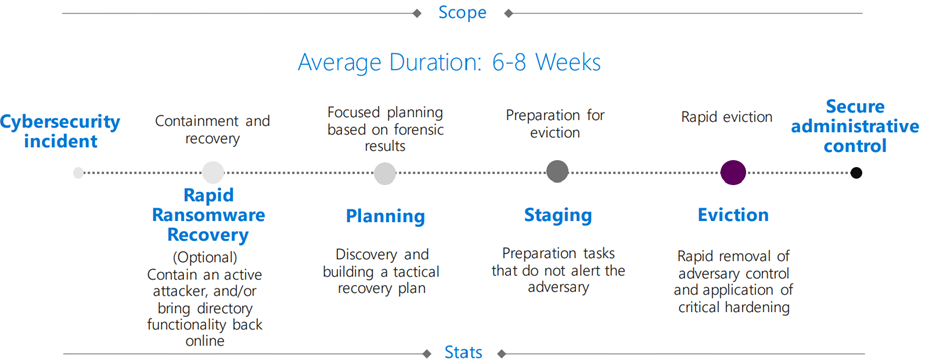
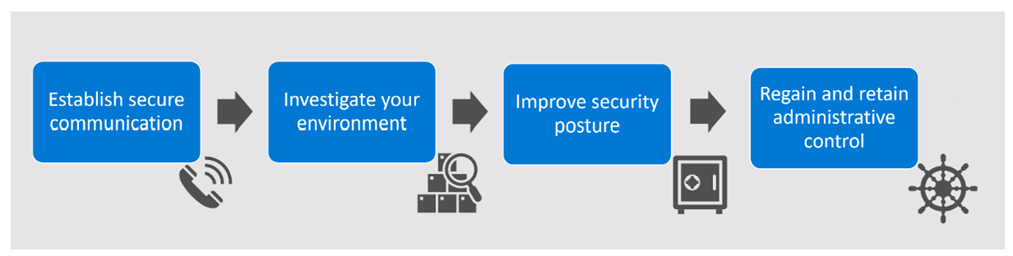
In compromise recovery, the most important first step is always restoring the authentication services and limiting the effects of ransomware, for instance. This is how our experts normally proceed:
Strategy is the victor: monitor and quickly remove attackers
If attackers are already in the system, first and foremost it’s important to understand how they got in, where they already are, and what exactly they’re doing – without them knowing that you know. Only then can they be removed in one quick action and locked out permanently. Successful compromise recovery rests on multiple pillars:
- Detect the scope of the compromise by detecting and evaluating incidents and risk indicators, for example.
- Tactically monitor attackers using appropriate threat protection products.
- Tighten up systems through appropriate controls in order to reduce the area susceptible to attack of users with high-privilege access and thereby prevent attackers from taking control again.
- Drive attackers out of the systems quickly while simultaneously providing newly structured systems.
System segmentation is essential here. Prioritization is simpler and new systems can be prepared to fit requirements. With its processes and procedures, administration is always the top priority: attackers absolutely want to access it in order to gain comprehensive control. And when an attack is successful, system administration has usually already been infiltrated.
In order to prevent future attacks, it’s important to introduce appropriate monitoring tools and train their users accordingly. This is the only way for the responsible parties to recognize risks in the company and learn what they have to pay attention to. In compromise recovery, this may be associated with an analysis of the attack and the tactical monitoring of the attackers. Administrators find out directly why the attack was successful – and how to make it as undesirable as possible in the future for attackers to attack, for example through multi-factor authentication.
Help in the worst case scenario – with a lasting effect
With professional compromise recovery, the entire infrastructure does not have to be completely restructured. This makes companies ready to back to work faster after attacks. A clearly improved administrative environment and new security processes will also ensure more security for the long term. The advantages:
- Rapid recovery of control over your own systems
- Heightened perception of risks for early defense against attacks
- Effective controls and security for highly privileged identities to avoid additional successful attacks
Cybercrime and cyber spying are more topical than ever. Even under the best conditions, a successful attack can occur at any time. As a participant in the Alliance for Cybersecurity and member of the Microsoft Intelligent Security Association, Skaylink is a recognized expert in this field. We’re certified for both AWS Security Services and Microsoft Identity & Access Management and Threat Protection. Compromise recovery is an everyday activity for our specialists. Are you acutely affected and urgently need help? Or do you want to proactively get your systems up to the most current status? We are there for you! Just get in touch with us.
Checklist: The most important actions after a cyberattack
- Do you and your organization have the requisite knowledge for analysis and recovery? Get the support of experts for threat intelligence or providers of malware analyses in the beginning stages of the attack. Also get into contact with the responsible law enforcement authorities.
- Check your systems in order to find out where attackers are already present.
- First restore enterprise-critical systems. Absolutely ensure that you analyze your backups for corruption before they are used for restoration.
- As soon as the enterprise-critical systems are back in operation, restore the other systems. Specialists in compromise recovery can support you with effective prioritization.
- Bring your security standards up to the most current version and remember to appropriately train users in order to avoid new attacks.